East SIG Report November 2021
27th February 2022
Neil Miller
Host Paul Woolard opened the November meeting, again from home via Zoom. The first presentation of the night was George Skarbek presenting his usual Q&A segment. With most members on their computers during the latest lockdown, many questions followed.
Q. Every time I start up Windows 10, File explorer starts by default. This is more an annoyance, rather than a problem. File Explorer is not shown in the Windows StartUp folder, so I feel the next alternate is to look in the registry, which I’m reluctant to do. Do you have any ideas what may be happening?
A. You’ve done the first thing I would have done, by looking in the StartUp folder. I know people are often scared to go into the registry, but I say don’t be afraid, go for it. The reason people are afraid is they don’t understand what the Registry does. The second reason is that there is no Windows “Are you sure?” warning or no Undo when making changes. When you do something in the Registry, Windows doesn’t check it won’t cripple or destroy your computer.
What you should not do in the registry is to delete a tree. Anything on the right side of the screen (right hand panel) you can delete, modify or edit without any real worries. I can’t think of anything you do on the righthand side that will have any serious impact on your computer. If you’ve found a hack on the internet to stop File Explorer opening, I say go for it.
[Reply] If I make a mess of things, will Windows rectify itself?
[George] No, that is why it’s good practice to take a backup of the registry and know how to reinstall it from the backup.
[Stewart Gruneklee] If you have a USB drive attached to your computer, that may be causing File Explorer to open. When you boot your computer next, see which folder on your computer File Explorer is open on. That could assist to identify the cause.
Q. I assume, a system restore won’t backup the Registry, but a backup will?
A. Yes, that is correct. When using backup software like Acronis, you can bring back a single file, a folder, a group of files or the whole drive from your backup. Therefore, you don’t have to replace the whole drive from the backup to reinstall the registry.
Q. What are the circumstances when you’ll need to do something to the registry?
A. When something is not going right is the only time I’ve had to edit the registry. Like the issue above, when File Explorer is opening and is not in the StartUp folder. Task Manager is one tool I use a lot when looking to solve problems, rather than going into the registry.
Q. The only thing my Acronis backup won’t restore would be the BIOS, is that correct?
A. That’s correct, the BIOS has nothing to do with the Windows operating system. The BIOS tells the operating system how much memory you have, the addresses for the disk drives, how many ports you have and so on. That information then gets feed to the operating system at the time of start-up. Before that, the computer has no idea what operating system you have. The computer could be running DOS, a version of Linux or iOS.
Q. Do I really need OneDrive?
A. No.
[Reply] Good
Q. Can you give a brief outline on using the Registry?
A. George proceeded to give a brief overview of the registry. In the example he used below, it’s assumed the user is given a registry hack via a search engine
-
The registry is opened from regedit.exe as follows.
Press Win Key + R and type “Regedit”. -
Regedit opens and displays the 5 keys shown in Figure 1.
-
Selecting HKEY_LOCAL_MACHINE opens a long list similar to a tree in File Explorer. George clicks on DirectX and selects an item from the right panel and right clicks on the entry.
-
A dialogue box opens giving options to Modify, Delete or Rename the item. George selects “Modify” and a dialogue box (Figure 3) opens where the DWORD value can be changed from 1 or 0.
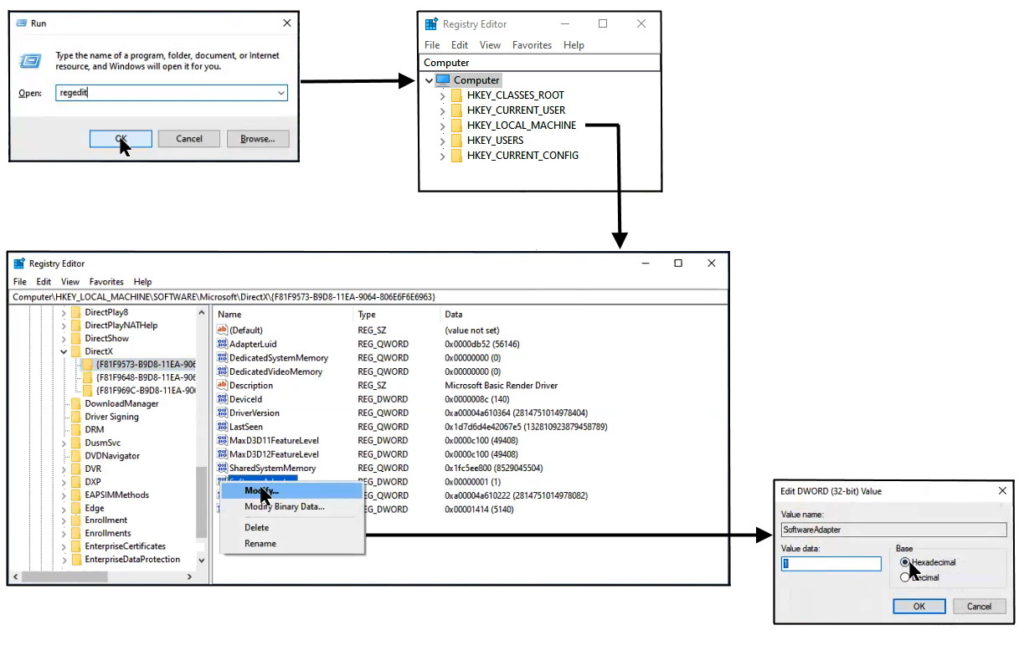
Figure 1 – Steps used to modify entries in the Windows registry.
-
The registry is a hierarchical database that contains data that is critical for the operation of Windows and the applications and services that run on Windows. The data is structured in a tree format. Each node in the tree is called a key. Each key can contain both subkeys and data entries called values.
The registry contains two basic elements: keys and values. Registry keys are container objects similar to folders. Registry values are non-container objects similar to files. Keys may contain values and subkeys. Keys are referenced with a syntax similar to Windows’ path names, using backslashes to indicate levels of hierarchy. Keys must have a case insensitive name without backslashes.
The 5 Keys are:
- HKEY_CLASSES_ROOT.
– contains information about registered applications - HKEY_CURRENT_USER.
– stores settings that are specific to the current logged-in user. - HKEY_LOCAL_MACHINE.
– stores settings for hardware & software that are specific to the local computer - HKEY_USERS.
– stores settings for each user profile actively loaded on the machine, - HKEY_CURRENT_CONFIG.
– Stores details about the current configuration of hardware attached to the computer.
[Source Wikipedia]
- HKEY_CLASSES_ROOT.
Following Q&A, Trevor Hudson played one of his videos titled “Add-ons to make Firefox more Private”. (Refer https://www.youtube.com/watch?v=rZGhwAgkE1U).
The video commences showing each step needed to install each of the 4 add-ons Trevor recommends to make browsing more private. The 4 add-ons Trevor installed in the video are, “uBlock Origin”, “Self-Destructing Cookies”, “Privacy Badger” & “HTTPS Everywhere”. Prior to installing each add-on, users can read what each add-on does and then decide if they wish to continue with the install.

Figure 2 – Opening scene from Trevor’s video
With the 4 add-ons installed, Trevor gives 4 further privacy tips.
- Select and use Firefox’s New Private Window.
- Open Firefox’s Application menu, select Settings then General. For extra privacy select Firefox as the default browser.
- Open the Application menu again, select Settings then Search. In the list of browsers in the dropdown list select “DuckDuckGo” as the default search engine. This will improve your privacy and stop advertisements.
- Open the Application menu once more, select Settings then “Privacy & Security”. Here you can decide on your preferred privacy settings.
The next presentation was by Dave Botherway with a “Sequel to Internet Shopping”,
from last month’s presentation titled “The scam aspects of on-line Shopping”.
The presentation commenced by summarising “Story 2” from last month’s East SIG meeting. Story 2 from that meeting is copied below.
-
Story 2 – A legitimate story on Facebook reporting the sale of outdated Dell Inspiron 17” Laptops appeared following Microsoft’s announcement it would no longer be supporting Series 7 CPU’s. The article stated these laptops were being sold at bargain prices to clear old inventory. As there was possibly some truth to the offer, Dave tried a second attempt knowing PayPal would protect him if this was another scam. Contacting the seller about the progress of the sale again proved fruitless, so another claim was made on PayPal. The claim was readily accepted and the refund was back into his bank account in two days.
An interesting aspect of this story was after the PayPal claim was accepted and a refund received, an email arrived from the seller with a genuine tracking link. Dave followed the tracking link each day and finally a parcel did arrive. When opened, the parcel revealed a small pillow case or cushion cover, not the laptop he ordered.
Dave’s investigations on internet scams sparked his interest in 2 in 1 laptop computers. Eventually Dave spotted what he felt was a genuine bargain and purchased a 2 in 1 from Dell. Details of the purchase are summarised below:
- One of the 2in1 models that took Dave’s interest was a Dell Inspiron 15. [Specifications: 11th Generation Intel Core i7-1165G7 Processor, Windows 11 Home, Intel® Iris® Xe Graphics with shared graphics memory, RAM 16GB. 2x8GB DDR4 @3200MHz, 512GB M.2 PCIe NVMe Solid State Drive with a 15.6” touch display.]

Figure 3 – Dell Inspiron 15 2in1 Laptop
- On Saturday 23rd October Dell was selling Inspiron 15 2-in-1 Laptops at $2,949. Dave felt this was too expensive, but kept watching the Dell website.
- A few days later Intel announce their new Gen-12 CPUs.
- On Wednesday 27th October Dell was clearing Gen-11 Devices, selling the Inspiron 15 at $1,621.99, a saving of $1,327 or 45% off.
- Dave felt this was a bargain and using PayPal, made his purchase on the Wednesday night. The Dell Inspiron 15 arrived on the following Friday.
- A few days later the price had returned to the pre-sale price of $2,949 and at the time of this meeting (11th November) the price was back to the sales price.
In summary, when making internet purchases, Dave recommends members watch for technology changes, new products and events such as Black Friday and Singles Day sales. Suppliers are often keen to quit old stock hardware, computers that cannot run Windows 11, or old model Gen-11 CPU’s, as was the case with Dave’s purchase from Dell. Margins are often irrelevant for old stock.
The next presentation was from Phillip Lynch. Phillip is a member of the GWS (Google Work Space) Transition Team who are moving all emails from the Microsoft server to the Google Work Space. The club will reach a milestone at the end of the month (November) where all emails previously coming into the melbpc.org.au domain via the Microsoft account, will go directly to the Google Work Space account.

Figure 4 – Google Work Space
After November members will still be able to use their Microsoft account to send emails out, but they won’t receive any new emails. Eventually access to the Microsoft account will end completely. Phillip asks members who are still using their Microsoft account if they could move over to GWS now. Instructional videos are on the MelbPC website and team members are available to help members if needed. A selection of questions asked of Phillip are shown below.
Q. Do we need to do anything if I’ve never used the MelbPC email and now pay Microsoft direct for Microsoft365?
A. If you’ve never used MelbPC email you don’t have to do anything. I assume messages will have been sent to that email address, but they will just sit there.
Q. How would I know if I’m still using my Microsoft account? If I’ve not heard from the transition team, does that mean everything is okay?
A. There are 2 ways that you would know. Come December, if you are not receiving any emails, then you haven’t transitioned.
Phillip then asked the member how he currently accesses his emails, via a web browser or an app on his computer?
(Reply: I use Outlook) Phillip offered to look up his records and advise the member
Q. Can I send an email to myself to see if I’ve transitioned?
A. No, because it will arrive via the Microsoft account then to GWS.
Q. Will Thunderbird now automatically pick up the Google setting rather than Microsoft, or do we have to enter the settings manually?
A. You will have to change the server settings and it depend whether you get emails by imap or POP. The transition team have helped many members do this. We have built up substantial expertise transiting Thunderbird users.
Q. Does MelbPC have ability to reset the GWS password if any member forgets it?
A. Yes, MelbPC admin can reset your password. However, you can do this yourself and it will be quicker. If you’ve put in a recovery email address (that is a non MelbPC address) or mobile phone number, you can do it yourself. Go into Google “Forgotten Password” and Google will send you a link to your phone or recovery email address, with a code that will allow you to change your password. That is the best and quickest way.
Q. For those members like me who still using Eudora, an email client which hasn’t been supported since 2006, you will find it still works after the transition to GWS and also works on Windows 11.
A. I’ve heard there are a few members still using Eudora.
With no further questions forthcoming, Phillip proceeded to explain the technique he uses to quickly assess his Google Web Space. This technique is called progressive web apps or PWAs and has been around for a few years. Not all websites are configured for this technique, but the number of sites is growing. It’s part of the browser where you turn that particular website into an app.
You can do this with Gmail where you turn the website into an app. This technique makes an entry in your Windows program files and creates an icon for the PWA. You can then drag the icon onto your desktop or onto the taskbar. When you click on the desktop icon, you’re automatically logged in.
With progressive web apps there’s no address bars and baggage of the browser, but it’s still the browser working. The beauty of this with Gmail is you can elect how much of your email you wish to save on your local machine, none of it, some or all of your emails. Gmail as a PWA is quite fast, intuitive and you get access to all the GWS features. If you only have a MelbPC account and running a recent version of Windows, setting up your browser as a progressive web app is a really good way of accessing your GWS account. It’s not like webmail, is a really good way of accessing your Gmail and it’s very fast.
In Chromium based browsers such as Chrome, when on a website that has PWA functionality, you’ll see an “Install [site name]” when hovering your cursor over the icon at the end of your address bar. This looks like a monitor with a down arrow in front of it. When you click the icon, Chrome will display an “Open with” [site name] pop-up.
If you wanted to install YouTube as a PWA, click “Install YouTube” as shown in Figure 5, to install the website’s PWA on your PC. The app will automatically open in a new window and a shortcut will be added to your Start menu and desktop. Double-click on the desktop shortcut to launch the PWA without having to open your browser first. You can also pin the app to the Windows taskbar for easy access.
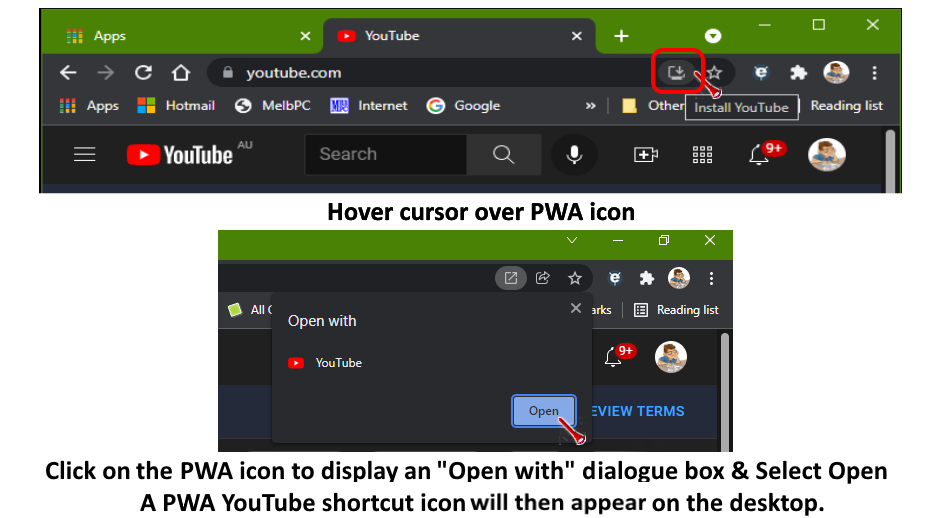
Figure 5 – Installing YouTube as a Progressive Web App.
The final presentation was by Stewart Bedford on his new home security camera system.
Some years ago Stewart installed a security camera system on his home. This system was an IP system where cameras could be connected by either by WiFi, Ethernet cable or PoE (Power over Ethernet for power and recording) to a NVR (Network Video Recorder) or computer. Stewart installed his original system himself and adopted the WiFi option to avoid the need for ethernet cabling. This option required the cameras to be powered, which Stewart did by connecting to a power point inside the house. The camera then sent data by WiFi to his computer. The IP cameras needed a fixed IP address, which caused problems when his Internet Service Provider randomly change his IP address. This caused the cameras to go offline. Stewart then needed to go back into the cameras setting and enter the new IP address. As the system was becoming outdated and restricted to where cameras could be located, Stewart started investigating upgrading his system to newer technology.

Figure 6 – Stewart’s Original IP Camera
After extensive research, Stewart settled on a Eufy Cam 2C security camera setup. He purchased a 2-camera system for $399 (Figure 7 & 8), plus an additional camera for $183.00. This system uses WiFi, is battery powered, is subscription free and is easy to install oneself. Being battery powered, the cameras do not need mains power from inside his home, as Stewart’s previous system did. This allowed installation at more appropriate locations than previously.
Specification of the Eufy Cam 2C
- The standard kit comes with a Homebase to store recorded videos and 2 cameras.
- The capacity of the Homebase is 16GB.
- Camera resolution is 1080P video which is full HD quality recording
- Cameras have a 135o field of view
- Cameras are battery powered
- Cameras connect to the Homebase by WiFi
- All controls are entered via the EufySecurity app.
- Cameras record day and night time infrared vision with motion activation.
- The cameras have built-in microphones so record audio and allow two-way conversation.

Figure 7 – Eufy Cam 2C Security Camera Kit
Setting up the Eufy Cam 2C
Stewart found the Eufy Cam 2C easy to setup. Because the cameras were battery powered, he was not restricted to where cameras were located, as he was with his previous setup. As the cameras connected to the Homebase by WiFi, mounting locations could be confirmed prior to permanently mounting the cameras. The only proviso was that the cameras’ WiFi signal had to reach the Homebase, which was connected to Stewart’s router, located at his computer. If this had been a problem, the Homebase could have been moved away from the router. The Homebase would then use its WiFi to connect to the router. In this situation the Homebase acts as a WiFi extender and has a range of 15 metres. When locating the cameras, one disadvantage was that periodically they had to be taken down to be charged. This meant they could not be mounted so high, that they could not be easily reached with a short ladder. Charging of the cameras is done by connecting to the Homebase or via a phone charger. Eufy claim that batteries can be re-charged 300 times and last approximately 5 years, depending on options set via the EufySecurity app.

Figure 8 – Eufy Cam 2C Security Camera Kit
Features and Optional extras
- All controls are via the EufySecurity app.
- The cameras can record sound and when used in live mode the homeowner can conduct two-way conversations.
- Live streaming is available, but results in higher battery use. Stewart adopted motion activated recording instead, as he didn’t feel he needed continuous recording.
- The EufySecurity App will send alerts of activity to your phone. Stewart found this annoying and sometimes turned it off while still receiving silent text alerts.
- Recordings are stored on Homebase or at an extra monthly cost of $4 in the cloud.
- According to Eufy the Homebase will overwrite stored video files when capacity is reached. Stewart has manually deleted files a couple of times so has yet to reach capacity.
- A maximum 16 cameras can be added to the system
- Remote viewing and control is via the EufySecurity App.
- Cameras are battery powered with a life of 180 days depending on use. More recent models have 1 year battery life per charge.
- Batteries can be re-charged 300 times which is approximately 5 years.
- The EufySecurity App displays when batteries need charging
- Cameras have a built-in spotlight to record in colour at night.
- A 100dB Siren can be set on the camera, Homebase or both, via the EufySecurity app.
- Optional solar panels are available to re-charge the camera’s batteries.
- The motion activation limit is 8 to 10 metres maximum
- Face recognition and human body shape detection can eliminate the camera from activating unnecessarily.
- The field of view of the camera can be narrowed to eliminate activation from trees blowing in the wind.
- Included in the kit is a ball and socket wall mount.
- The camera is light in weight and small in size so can also be mounted using a magnetic base or double-sided tape.
- Cameras are waterproof.
- Data is secured with 128-bit video encryption. Data stored on the homebase is completely private so it can only be accessed by the owner.
- Cameras can be moved inside temporarily if wished to watch misbehaving pets etc.
- There are many other features that Stewart didn’t have time to detail.

Figure 9 – Eufy Cam 2C Camera
Advantages of the Eufy Cam 2C
In addition to many of the features mentioned above, Stewart sees the main advantages of the Eufy Cam 2C he installed is its do-it-yourself installation. This is due to the battery powered cameras which avoids the need for professional installation of cables & wiring. Storing data onsite was also an important consideration. Stewart’s system of 3 cameras and Homebase was purchased for under $600, compared to many thousand dollars for a professionally installed IP camera installation.
Throughout his presentation Stewart played a number of videos taken with the Eufy during the day and at night. The resolution of the videos was excellent as can be seen in Figure 10 below. The ability to easily relocate cameras to suit certain situations was an added bonus.

Figure 10 – Eufy Cam 2C Capture from Stewart’s video
Disadvantages Eufy Cam 2C
The battery powered cameras are the major advantage of the Eufy Cam 2C, but also its major weakness. It will depend on how users prioritise this feature whether the Eufy Cam 2C is appropriate for them. Cameras need to be removed for re-charging and batteries are not replaceable, which means the system will have a finite life. According to Eufy, cameras can be re-charged around 300 re-charges, which is fine for motion activation recording. The Eufy is only suitable for motion activation recording. For continuous recording you will require a different system.
Stewart’s Conclusion
Stewart’s security camera system has been operating for over a year now and it has performed perfectly over that period. Video quality is good, as the videos he displayed during the presentation showed. The 16GB capacity of the Homebase has been more than adequate for his needs and selecting a battery powered camera system far outweighs any negatives.


